A few days ago I’ve came across an interesting Cyber security press release over at marketwatch.com and suddenly I was struck that as of today there is no product on the market that can automate pentesting for business Logic.
Most products are human based pentester or encapsules different methods of pentesting.
After a little bit of searching I found that BLST Security (a young start-up in the cyber security field) claims to be able to do that with integrated Artificial Intelligence.
Today, I’m reviewing Firecracker v.1by BLST Security, a CLI tool that protects organizations from logical flaws.
Firecracker provides an intelligent attacker that simulates business flows in your API. The CLI tool provides detailed analyses of existing attack surfaces, vulnerable flows, and simplifies the architecture of the API.
The company released their first CLI tool, the free version is available at http://blstsecurity.com/firecracker and the open sourced code is available at https://github.com/blst-security/firecracker.
After a quick look in their GitHub page, it looks like a simple to use CLI tool. The main goal of this tool is to attack your API and scan for invalid business logic flaws, as a secondary value it can also produce a map of your current API
structure and show you the logical connections between different endpoints and parameters.
The product suits any stage in the SDLC – Software Development Life Cycle.
Let’s dive deeper.
The tool is delivered in a Binary version. It’s a perfect solution for me as I won’t need to install Rust nor build the open sourced code.
Installing Firecracker
Inorder to install the tool we need to use git with the following steps:
`git clone https://github.com/blst-security/firecracker
cd firecracker
cargo build –release`
Or we can just download and install the binary version in https://www.blstsecurity.com/firecracker
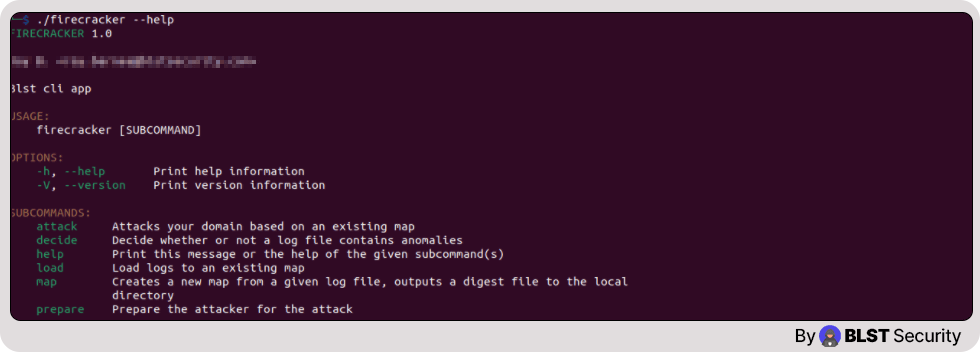
We can start by reading all the given possibilities using the help flag ./firecracker –help
Before we use firecracker binary we need to import our token from the BLST Security website.
Firecracker features
Firecracker has several features:
Mapper
Takes in traffic logs and maps the business logic flow of the application, outputs a digest file.N
Decider
Takes in traffic logs and decides whether a certain business logic flow is an anomaly or not.
Attacker
Takes in the digest file from the mapper and “attacks” the API while using the Decider to determine whether something is an anomaly or not.
Visualizer
Takes in the digest file from the mapper and visualizes the business logic flow of the application.
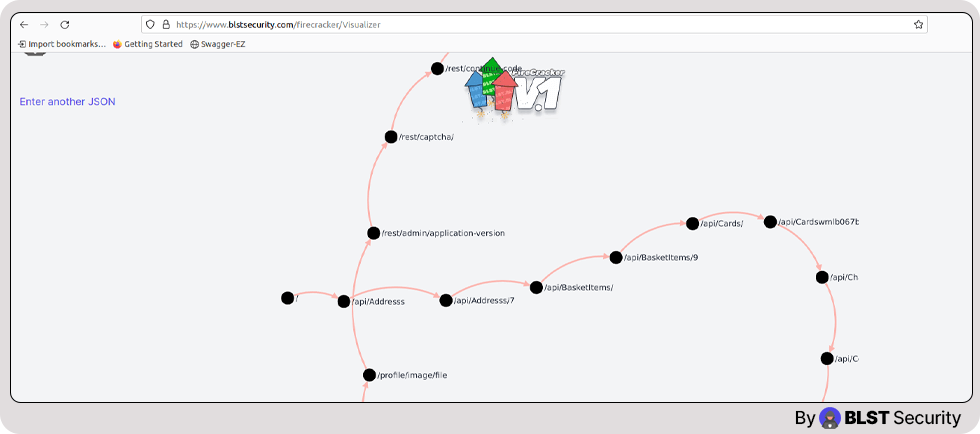
So the Mapper is supposed to receive a log file formatted in json, and then it will map it.
After the mapping is complete you can take your map file (the default name is map.json) and upload it to the following address – https://www.blstsecurity.com/firecracker/Visualizer in BLST Security’s website.
After mapping the API we will use the attacker (the automatic penetration tester), his aim is to spoof the current request conventions by sending in different API logic flows and fuzzing the parameters.
Before we start the attacker we need to prepare it using the prepare command
./firecracker prepare –url https://blstsecurity.com –map map.json
while maintaining the following format
“firecracker prepare –url <URL_TO_ATTACK> –map <MAPPED_FILE_PATH>”
Release the attacker
Then launch the attacker module:
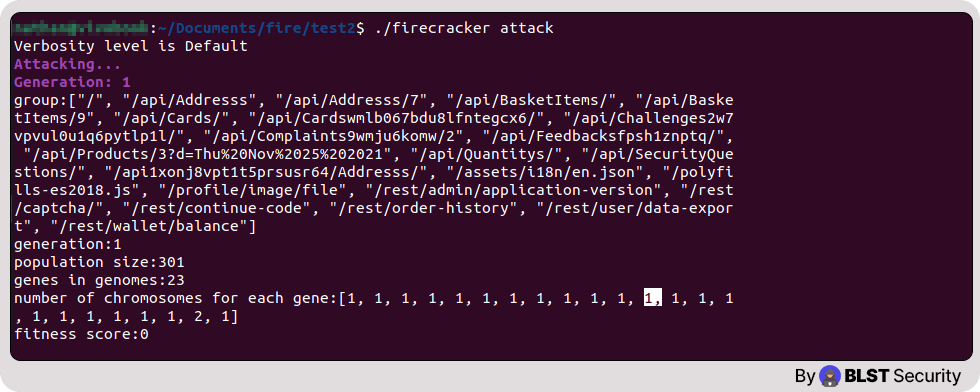
./firecracker attack
At this point we can see if anomalies were discovered and outputted in the current attack generation
There is another option in which you can use the decider as a stand alone without the attacker and load other users logs into the decider and see whether or not anomalies exist in your current user logs and data without launching an attack against your API.
Copy and execute the following command to activate the decider and test your existing logs.
./firecracker decide –file log.json.
In conclusion
I give this tool 5 stars, the CLI tool is very intuitive and simple to use.
From a technical view the CLI tool provides immense value in a short amount of time with very few false positives and produces outstanding results.
In my opinion The key values that this product provides are:
- API Logic visibility
- User behavior anomaly detection
- Easy installation and integration into current environments
- Advanced security testing
- Intuitive interface