API vulnerability overview
APIs are becoming an integral part of business and web application development, but this growth has been accompanied by a rise in insecure API implementations that can expose companies to hackers, DDoS attacks, data loss, and eventually economic loss. The security of your APIs is a critical part of the success of your company -understanding the common API vulnerabilities is crucial.
The most common way to get access to private data is by taking advantage of insecure or unsecured APIs. This is why your API should be secure and difficult for hackers to break into. But, there are many ways that you can get hacked by an attacker who wants to steal data or take down your system. With a little bit of knowledge, you can easily protect your API from attacks and keep your users safe.
In this article, we’ll show you 8 common API vulnerability types that can be found in almost any API and how to avoid them, so you can keep hackers out and improve the overall security of your application for your company and business.
Let’s dig in…
OWASP’s top10 vulnerabilities?
The OWASP Top 10 is a list of the most common and dangerous application security vulnerabilities. OWASP is a non-profit organization that works to make web applications and web servers more secure. The web app vulnerabilities are described as “the ten most critical web application security risks.”

Learn more about API penetration testing
What are the 8 common API vulnerabilities?
These vulnerabilities are very common in web-based systems and allow hackers to easily access a company’s information by breaching or manipulating these types of security protocols. In a list of vulnerabilities, we have gathered the top 8. In our opinion, these are the crucial ones. Some of these vulnerabilities can be resolved with proper planning and using new tools and reference architectures, but others might require a complete protocol overhaul that may or may not be possible, depending on the scope of a specific system API, integration points, and capability of the human factor.
Our 8 common API vulnerabilities are:
- Broken Object Level Authorization (BOLA)
- Broken User Authentication
- Improper Asset Management
- Excessive Data Exposure
- Lack of Resources & Rate Limiting
- Broken Function Level Authorization
- Mass Assignment
- Injection
Broken Object Level Authorization (BOLA)
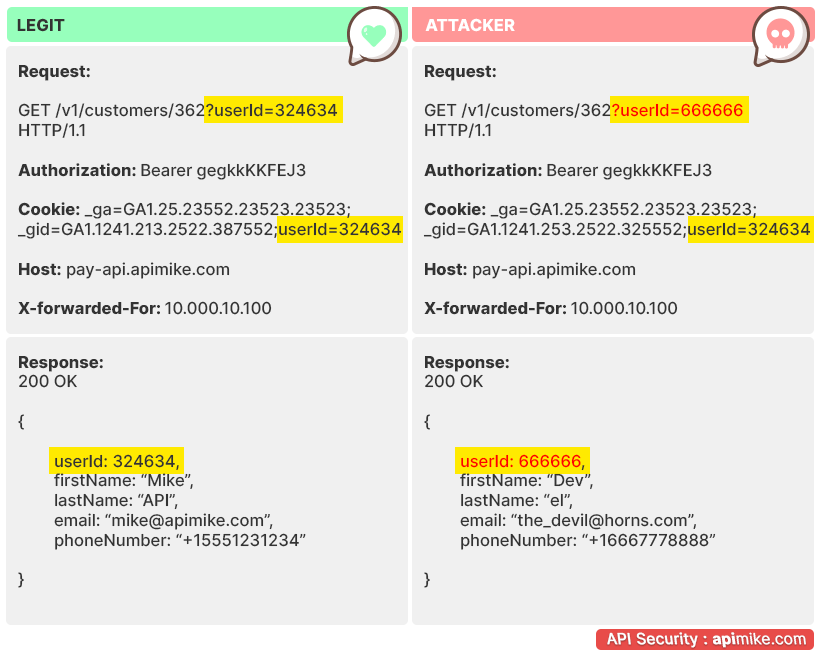
A BOLA API vulnerability occurs when sensitive fields within an object are incorrectly exposed. This is a result of the server component’s failure to fully follow the client’s state and instead relying more on the object IDs sent from the client to decide which object to access.
For example, if a user’s personal information is not securely protected within an API response that is sent back to the user’s browser or mobile device, attackers could use this information to impersonate the authorized user and gain access to their account. This issue is common in API-based applications.
Uber’s API was breached a few years ago. This was reported by Anand Prakash in his article about The Uber API Authorization Vulnerability.
Can I prevent it?
A way to prevent BOLA attacks is to allow an API security solution to be able to learn the business logic of an API and detect when one authenticated user is trying to gain unauthorized access to another user’s data.
Broken User Authentication
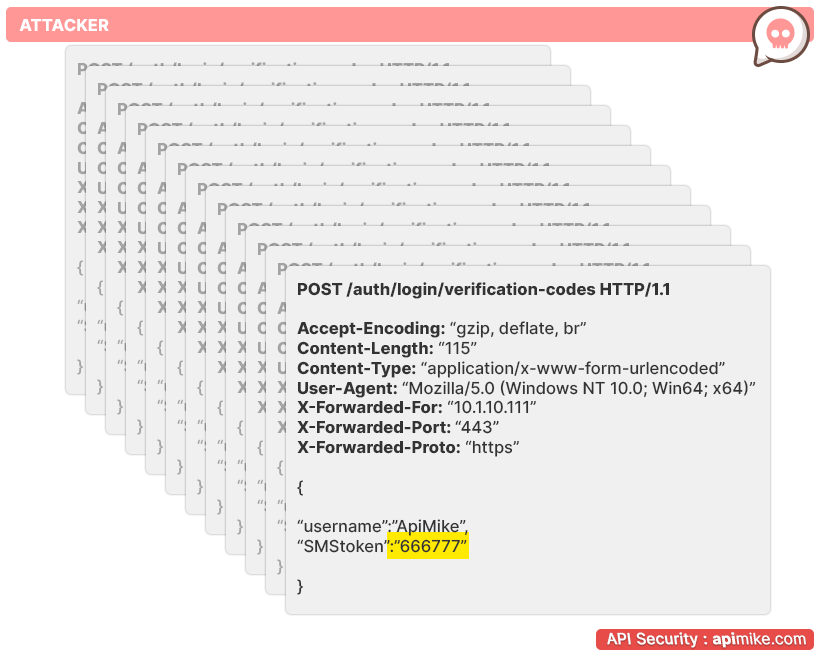
When valid credentials for the system are not required for an API request, that is likely to be a “Broken User Authentication” issue. If the API doesn’t require any authentication, it can be used by attackers to gain unauthorized access to protected resources.
For a business, this kind of problem may present a critical challenge since the improper implementation of the authentication process may result in unauthorized access to sensitive information and computer systems.
Can I prevent it?
An effective API security solution must first profile the typical authentication sequence for every major flow. This enables it to detect abnormal behavior, including authentication calls that are out of sequence.
Improper Asset Management
This vulnerability arises when confidential information is insufficiently protected or not accessible at all within APIs. This makes it easy for hackers to discover and exploit the system.
For example, if we, as a company, did not protect our employees’ passwords with hashing algorithms, hackers could easily use publicly known hash algorithms to build targeted phishing campaigns against them. The goal of these campaigns would be to get victims’ login credentials in order to gain access to sensitive company data.
Can I prevent it?
API security solutions must be able to analyze all API traffic and continuously discover APIs. API traffic analysis should include the ability to identify all host addresses, API endpoints, HTTP methods, API parameters, and token data types, including the identification and classification of sensitive data and their values.
Excessive Data Exposure
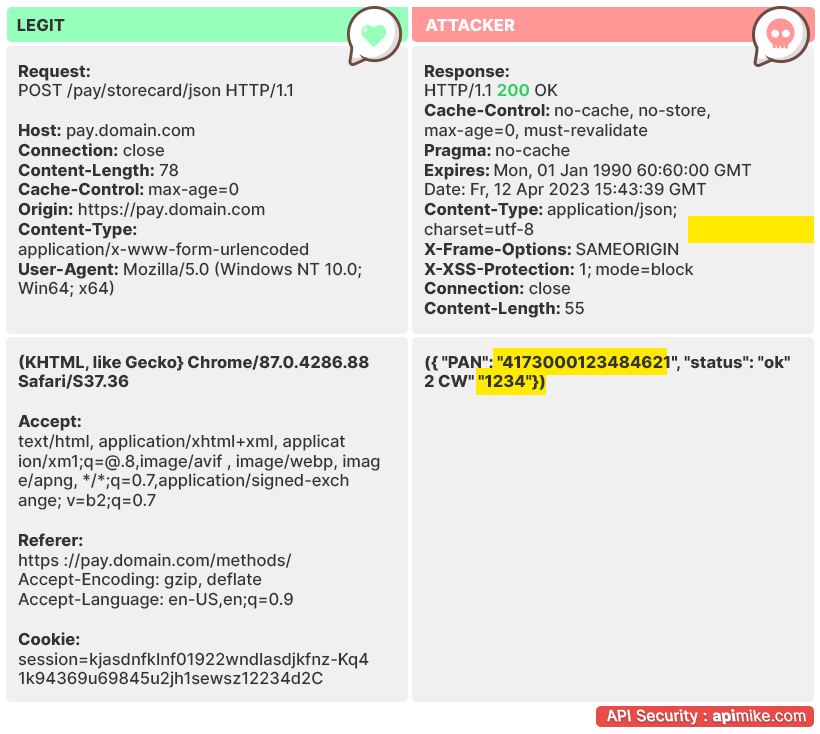
A system that has too many API endpoints enabled with excessively exposed data can be exploited by attackers. APIs should only include the functionality required for their intended purpose and nothing more.
Exposing too much information about existing or future products is counterproductive as it enables hackers to use the APIs to perform reconnaissance on them, which could result in stolen IP, lost revenue, and damaged reputation.
Can I prevent it?
Applying an API Security solution that is able to track endpoints, map, and identify excessive consumption of data per user.
Lack of Resources & Rate Limiting
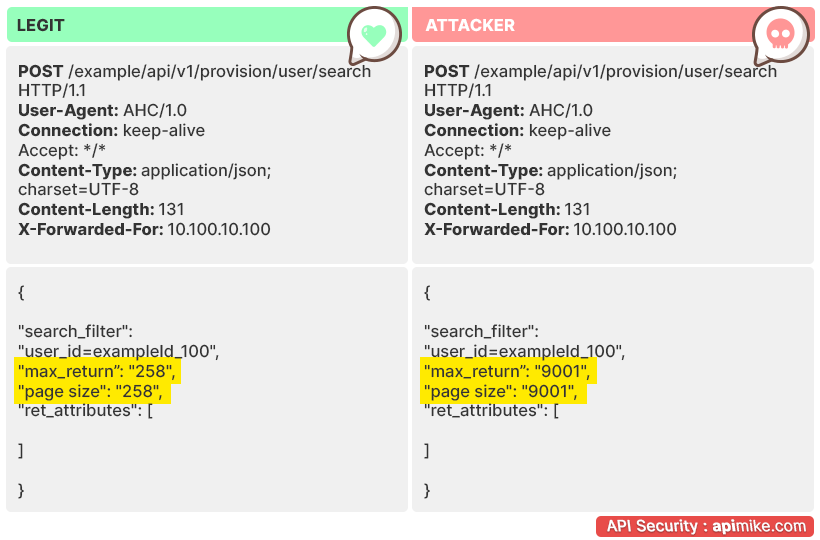
This vulnerability occurs when the API does not impose any restrictions on the number of requests made by a specific API client. This can be exploited by attackers who send an excessive number of requests to an API with the hope of exhausting its resources or slowing it down to a point where it can no longer be used.
If there is no limit on the number of requests that can be made to an API, or if the resources required to process them are not controlled, then it could leave the system open to abuse.
Can I prevent it?
Identify API endpoint modifications that are breaching the day-to-day usage. This can be done by analyzing the normal usage of an API.
Broken Function Level Authorization
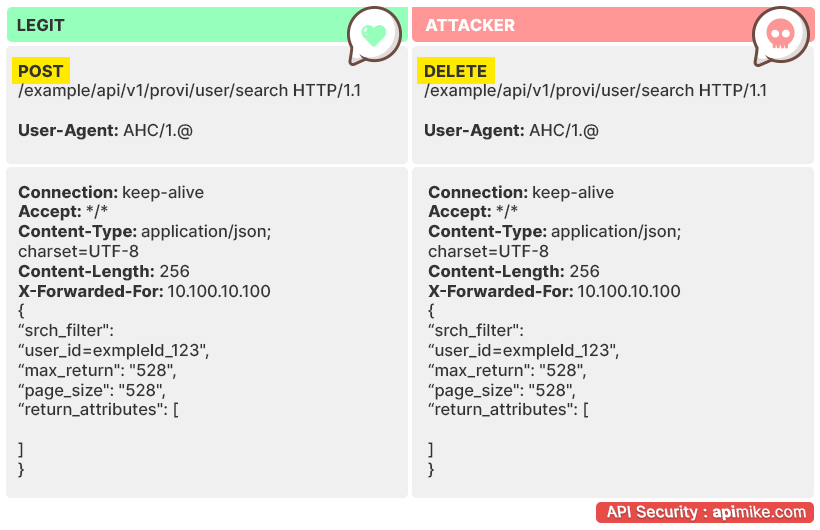
This vulnerability occurs when certain functions within an API are not properly authorized, which could allow unauthorized users access to sensitive data and systems. Attackers can exploit this vulnerability by calling APIs that are intended to be used by one actor but used with malicious intent by another.
For example, if I send a request as a regular user of an application to perform an authorized user function and it goes through, then that means the vulnerability is present and the system is violated.
Can I prevent it?
Anomalies, such as unusual parameters sent to a specific API endpoint, can be pinpointed and discovered within these boundaries.
Mass Assignment
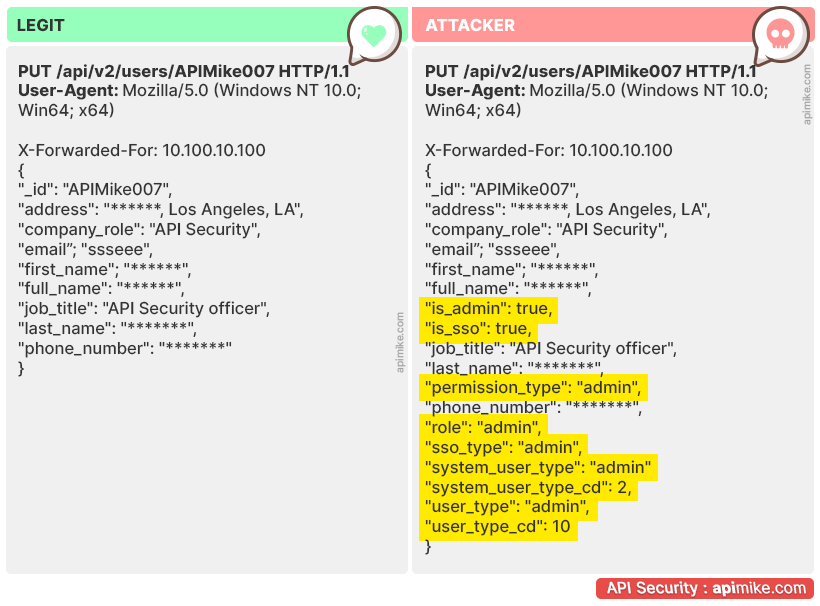
Here we have injection. This is a vulnerability that occurs when untrusted data is inserted into an application in such a way that it executes unintended actions or accesses sensitive data. Injection attacks are very versatile and can be used for a variety of purposes, such as stealing data, conducting reconnaissance on the target system, or even taking over the entire system of a company or business.
Can I prevent it?
An API security solution that can map normal behavior on a constant basis and identify anomalies that are outside the normal boundaries should be able to recognize the information gathering phase by a potential attacker.
Injection
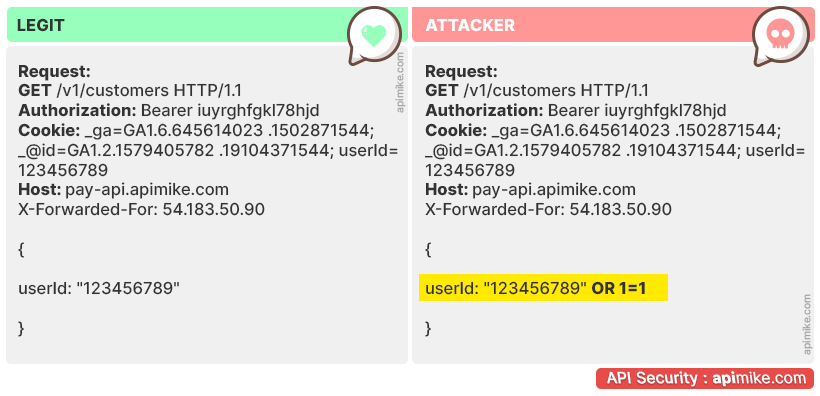
Here we have injection. This is a vulnerability that occurs when untrusted data is inserted into an application in such a way that it executes unintended actions or accesses sensitive data. Injection attacks are very versatile and can be used for a variety of purposes, such as stealing data, conducting reconnaissance on the target system, or even taking over the entire system of a company or business.
Can I prevent it?
An injection flaw can be maliciously used in almost every part of a request, like headers, cookies, query parameters, and the message body. It is required that these flaws be detected at an early stage of an attacker scan.
How to defend against these API vulnerabilities?
API vulnerabilities are generally becoming an increasingly important issue as more and more businesses rely on APIs to connect with customers and partners. As we’ve seen, these APIs can be exploited in a number of ways. However, there are simple steps that you can take to help defend against them.
- Make sure that your API is well-protected. Use strong passwords and security measures, and make sure that only authorized users have access. Make sure that all users have unique passwords and use strong authentication methods such as two-factor authentication. This will make it much more difficult for attackers to gain access to your API, and be sure to regularly review security measures in order to stay up-to-date with the latest trends.
- You should also test your API regularly for vulnerabilities. Developers need to take care to properly check all user input before using it in any application logic. You also need to properly control request volumes to prevent denial of service attacks and exercise caution when designing APIs to avoid exposing private or confidential company data. Make use of penetration testing tools to identify any weaknesses in your system, and fix them as soon as possible.
- Finally, keep up to date with the latest security threats and updates. Make sure you’re aware of any new exploits or vulnerabilities that could potentially affect your API and always verify that user input is coming from a trusted source before taking any actions based on that input. There are a number of resources available online that can help you stay up-to-date, such as the OWASP Top 10 for APIs and the Trustworthy Repositories Audit & Certification (TRAC) program.
Conclusion
In the world of APIs, security is paramount. If an attacker can manipulate a few lines of code to compromise your system, it opens up a variety of attack vectors for them to access data in a way they shouldn’t have access to. While APIs offer a wide variety of potential benefits for businesses and consumers, they can also be vulnerable to attack.
In this article, we’ve looked at 8 of the most common API vulnerabilities. Each of these vulnerabilities can leave APIs open to an attack, which can result in data theft, financial loss, or reputation damage.
Companies need to be aware of these vulnerabilities and risks and take the necessary steps to protect their APIs against malicious activities and violations. And if all this might seem like a hassle, we would like to make it much easier for you.
If you have any questions about API vulnerabilities or need a penetration testing consultation, please contact us.