API refers to how one firm communicates with another’s software inside. An API lets a third party, like Facebook, directly access portions of an outside program, like TikToks’ login kit.
Hence the appeal for developers from all over the interweb and the world.
API growth will continue to increase in popularity due to the numerous benefits it provides to developers. Growth through 2023 will be significant as more and more businesses move to adopt APIs in order to connect their various systems. We expect to see continued growth in the number of APIs being made available as well as increased adoption of existing APIs. Some examples of this growth can be seen in the following areas:
- More APIs will be made available by organizations in order to allow access to their data and services.
- Existing APIs will continue to grow in popularity, with more developers using them to access data and services.
- New APIs will be created to allow access to new data sources and services.
- organizations will continue to invest in API management solutions to help them control and monitor their APIs.
- APIs will be used by more firms to link their systems.
In a recent blog post by Google about 7 trends to watch in the API economy they made a statement that API’s are now the “crown jewels” of modern software development and to top that they said that “API security takes center stage”.
What is security testing in API?
API security testing involves testing the API for any potential security vulnerabilities that could allow attackers to gain access to sensitive data or disrupt the functionality of the API. This type of testing is important to ensure that the API is secure and cannot be exploited by unauthorized individuals. Checking an API’s security ensures no one can acquire their info or do anything else unsafe.
What can go wrong without an API security testing?
Whoa, the list of the things that go wrong is endless, and I’m afraid this article isn’t enough to encapsulate all those bad things. If an attacker is able to exploit a flaw in an API, they can potentially gain access to sensitive data or system resources. They may also be able to cause Denial of Service (DoS) conditions.
Preparation for an API security testing
In order to prepare for API security testing, you should first understand how the API works and what it exposes—documentation would be a great place to start. Secondly, you should have a good understanding of common security risks and how to test for them. Finally, you should have a tool or framework that can help you automate security testing.
API Documentation step
A great place to start would be by reading the documentation for the API. The reason for that is simple: API developers hate writing these docs as they are time-consuming and, secondly, they use automatic specification tools similar to OAS3 with the wrong assumption that they provide a bulletproof specification tool – well they don’t and this is a place to find those vulnerabilities.
BLST Security to the rescue, just a few days ago I learned that the company released a brand new online web API security scanner in which you can simply drag ‘n drop a JSON or YAML file to start an upload which automatically initiates a scan and you can view the result online.
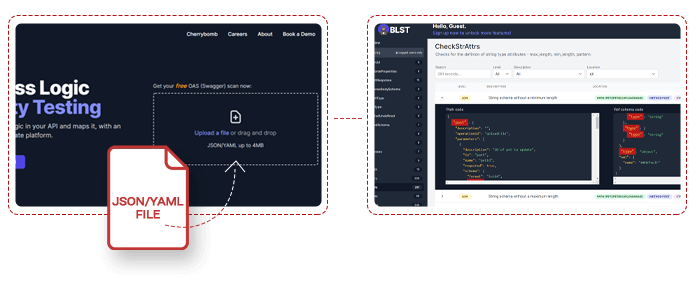
The result you will get and for free if I may add are phenomenal, you will get full list of the errors and their exact location that your specification might have, a params table, an EP (end points) table, and on top of that you will be able to produce a much secured API Documentation with this free online tool by BLST Security.
The API fuzzing step
Fuzzing is a technique that sends invalid or random data to an API in an attempt to crash the system or uncover security flaws. By crashing the system, an attacker could get access to sensitive data or take control of the API.
Fuzzing can be used to attack both the server-side and client-side of an API. Server-side fuzzing involves sending malicious data to the API server in an attempt to crash the system or access sensitive data.
An example of malicious data that could be sent to an API server during fuzzing would be a very large or infinite number of requests in a short period of time in order to overload the server. This could cause the server to crash or become unresponsive, disrupting service for legitimate users.
Client-side fuzzing, on the other hand, involves modifying the client-side code that interacts with the API. This can be done in order to bypass security controls or to inject malicious code into the system. You can use both server-side and client-side fuzzing to find security holes in an API.
This can be summarized as API fuzzing can be used to test for vulnerabilities in APIs and can also be used to test how well an API can withstand malicious input. Additionally, API fuzzing can help determine whether an API is flexible enough to allow for different types of input.
Some of the common API fuzzing tools are APIFuzzer, express-openapi-validator, OpenAPI Enforcer I’ll link these tools in the next section.
Planning the security testing approach and scope step
The approach and scope of API security testing will vary depending on the specific needs of the organization. However, some tips on planning the security testing approach and scope of API security testing include:
- Defining the API security testing security goals and objectives
- Identifying the potential risks and vulnerabilities associated with the API
- Determining the most effective security testing methods and tools for the specific API.
- Planning the security testing schedule and budget
API Attacker step
It is a common approach to hire a pentester for this step in the whole API security testing phase.
The pentester’s role in API security testing is to identify and exploit vulnerabilities in APIs. Reverse engineering APIs to understand how they operate lets them locate and exploit flaws.
Pentesters may also use automated tools to scan APIs for known vulnerabilities or to brute force their way into APIs. Once an attacker has access to an API, they can use it to launch attacks on the underlying application or database or to steal sensitive data. API security testing is a key part of making sure that web applications are safe, and pentesters play a crucial role in finding and taking advantage of vulnerabilities.

Learn more about API penetration testing checklist
A fresh technique is employing automated tools like the one BLST Security created, which is cost-effective and automatic.
It is an emerging application security method that links 2 phases in the SDLC pipeline. Scanning begins during testing/integration and generates a secure connection to real-time use data in production.
This approach can identify fraudulent business logic attack flows.
What tools were mentioned in this article?
BLST Security – https://blstsecurity.com
API Fuzzer – https://github.com/KissPeter/APIFuzzer
express-openapi-validator – https://github.com/cdimascio/express-openapi-validator
OpenAPI Enforcer – https://www.npmjs.com/package/openapi-enforcer
In conclusion
API Security testing is a difficult procedure that requires a strong grasp of methodologies and tools for fuzzing an API and attacking it on numerous vectors.
In this article, we had a fast recap of APIs and the emerging threats that they contain. We covered the steps one needs to take in order to conduct good API security testing and some of the tools that are available to perform this testing. Also, we added some new automated tools that any developer can add to the SDLC pipeline.